Hello everyone
I am running greenbone containers with gvmd version(25.1.1). Normal scans are working fine. I am trying to do authentication scanning with ssh key. Whenever I perform the authenticated scan it shows ssh authentication as unsuccessful in the report. I’m pretty sure I’m using the correct credentials and even manual ssh with the same private key from openvas server to target is working fine. No errors in the report or in the gvmd logs. I do see some errors like
error kex_exchange_identification connection closed by remote host
error kex_exchange_identification banner contains invalid characters
in the auth logs of the target machine. Please help!
You can check the manual to ensure you are using a supported private key format. Authenticated scans with Greenbone do not support the all the ciphers supported by OpenSSH.
Private Key
Upload of the private SSH key.
The key types Ed25519, ECDSA, RSA and DSA are supported.
The key must be in either PEM or OpenSSH format.
For DSA keys, only the OpenSSH format is supported.
To convert a DSA key from PEM format to OpenSSH format, the command ssh-keygen -p -f <private_key> can be used. This accepts the key in PEM format as input, requests the old passphrase (if one was set) and asks to set a new passphrase, which can be identical to the previous passphrase. The key is then saved in the default OpenSSH format.
Hi @rippledj
Thanks for the swift reply. I am using Ed25519 for ssh key generation and also the ssh key is in PEM format.
Where is the target system located on the network? By default, Docker containers can access the internet but cannot reach other hosts on the local network. This happens due to network isolation mechanisms implemented by Docker for security and operational control. To enable LAN access you need to enable macvlan support. However, the underlying host would be able to access the local network IP addresses under normal circumstances. So, that may be one cause of the issue.
Scan around the forum and you will find some posts about configuring this such as this post .
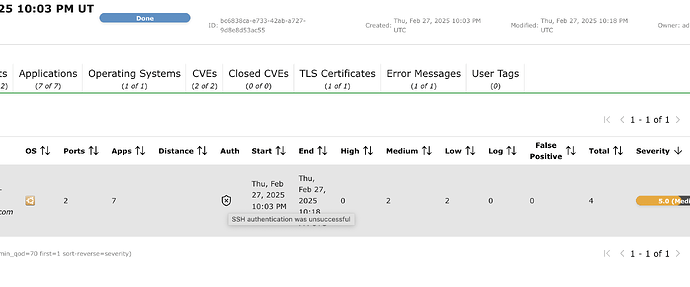
The target is accessed by its public IP. The below screenshot is from openvas running from the docker-compose file of community containers.
And I have another setup of openvas as a kubernetes deployment(created this issue for that). Its the same issue there as well. When I try to perform authenticated scan with ssh credentials the report shows ssh auth unsuccessful.
Can you please post the target host details including version of OpenSSH running on the target host?
Sure, the target is an ubuntu 20.04 machine. The openssh version is OpenSSH_8.2p1 Ubuntu-4ubuntu0.12, OpenSSL 1.1.1f.
Sorry, I’m just throwing out suggestions without really looking at the error message. I have not seen it before. Maybe I’ll have time in the next few days to look at it. ![]()
The only thing I can think of is that you are using some KEX algorithm that is not supported by Greenbone. But I can’t see why that would report as invalid characters.
You can see what the docs has to say about SSH Connections, both into the Enterprise Appliance and out to target hosts. But it is not clear about what algos are required for connecting out. I would guess that at least the KEX listed here are supported. You can check which ones you are supporting on the target host.
Only two short general notes:
- Greenbone Enterprise Appliance Manual: 10.3.5 Requirements on Target Systems with Linux/Unix lists some configuration options which could prevent a login
- The scanner is internally using
libssh(and notOpenSSH) for a login to the target- Which algorithm are supported by
libsshis listed (page is AFAICT only applicable for the latest version) at Features – libssh - For example the libssh version on the scanner host could prevent a login and/or cause other issues due to running:
- a too old version (e.g. a new algorithm required for the target host is not supported yet)
- a “buggy” version
- a too new version (e.g. an outdated algorithm required for the target host is not supported anymore)
- Which algorithm are supported by
Note that error kex_exchange_identification banner contains invalid characters could be completely irrelvant and originate from “service” / banner probing of the scanner / VTs.
Thank you @rippledj and @cfi for your insights. Until now I have tried using Ed25519 and rsa both are supported. And like manual ssh connection using the private keys are working. Also sshd config are in accordance with the requiements for ssh login in the greenbone doc. From my research on kex_exchange_identification(error: kex_exchange_identification: client sent invalid protocol identifier “GET / HTTP/1.0”) it seems like an issue on ssh client on openvas or on atleast how the ssh client is trying to connect to target. SSH client is attempting to connect using an HTTP request instead of the expected SSH protocol. Here are auth logs from target(maybe first 30lines) once I initiate an authenticated scan.
openvasscanner is the machine where openvas is running
scanuser is the user used for authenticated scanning
Feb 28 13:56:38 hostname sshd[331935]: error: kex_exchange_identification: Connection closed by remote host
Feb 28 13:56:44 hostname sshd[331938]: error: kex_exchange_identification: banner line contains invalid characters
Feb 28 13:56:44 hostname sshd[331939]: error: kex_exchange_identification: client sent invalid protocol identifier "GET / HTTP/1.0"
Feb 28 13:56:44 hostname sshd[331942]: error: kex_exchange_identification: Connection closed by remote host
Feb 28 13:56:45 hostname sshd[331940]: Received disconnect from openvasscanner port 63598:11: Bye Bye [preauth]
Feb 28 13:56:45 hostname sshd[331940]: Disconnected from authenticating user scanuser openvasscanner port 63598 [preauth]
Feb 28 13:56:45 hostname sshd[331943]: Received disconnect from openvasscanner port 63601:11: Bye Bye [preauth]
Feb 28 13:56:45 hostname sshd[331943]: Disconnected from authenticating user scanuser openvasscanner port 63601 [preauth]
Feb 28 13:56:53 hostname sshd[331947]: Connection closed by openvasscanner port 63618 [preauth]
Feb 28 13:56:54 hostname sshd[331949]: error: Protocol major versions differ: 2 vs. 0
Feb 28 13:56:54 hostname sshd[331950]: error: Protocol major versions differ: 2 vs. 1
Feb 28 13:56:54 hostname sshd[331951]: error: Protocol major versions differ: 2 vs. 1
Feb 28 13:56:54 hostname sshd[331952]: Connection closed by openvasscanner port 63624 [preauth]
Feb 28 13:56:54 hostname sshd[331954]: Connection closed by openvasscanner port 63625 [preauth]
Feb 28 13:56:55 hostname sshd[331956]: Received disconnect from openvasscanner port 63626:11: Bye Bye [preauth]
Feb 28 13:56:55 hostname sshd[331956]: Disconnected from authenticating user scanuser openvasscanner port 63626 [preauth]
Feb 28 13:56:55 hostname sshd[331958]: Received disconnect from openvasscanner port 63627:11: Bye Bye [preauth]
Feb 28 13:56:55 hostname sshd[331958]: Disconnected from authenticating user scanuser openvasscanner port 63627 [preauth]
Feb 28 13:56:56 hostname sshd[331960]: Received disconnect from openvasscanner port 63628:11: Bye Bye [preauth]
Feb 28 13:56:56 hostname sshd[331960]: Disconnected from authenticating user scanuser openvasscanner port 63628 [preauth]
Feb 28 13:56:56 hostname sshd[331962]: Received disconnect from openvasscanner port 63635:11: Bye Bye [preauth]
Feb 28 13:56:56 hostname sshd[331962]: Disconnected from authenticating user scanuser openvasscanner port 63635 [preauth]
Feb 28 13:56:57 hostname sshd[331964]: Received disconnect from openvasscanner port 63636:11: Bye Bye [preauth]
Feb 28 13:56:57 hostname sshd[331964]: Disconnected from authenticating user scanuseropenvasscanner port 63636 [preauth]
Feb 28 13:58:34 hostname sshd[331973]: error: kex_exchange_identification: banner line contains invalid characters
Feb 28 13:58:34 hostname sshd[331974]: error: kex_exchange_identification: banner line contains invalid characters
Feb 28 13:58:34 hostname sshd[331975]: error: kex_exchange_identification: banner line contains invalid characters
Feb 28 13:58:34 hostname sshd[331976]: error: kex_exchange_identification: banner line contains invalid characters
Feb 28 13:58:34 hostname sshd[331977]: error: kex_exchange_identification: banner line contains invalid characters
Feb 28 13:58:34 hostname sshd[331978]: error: kex_exchange_identification: banner line contains invalid characters
Feb 28 13:58:35 hostname sshd[331979]: error: kex_exchange_identification: banner line contains invalid characters
Feb 28 13:58:35 hostname sshd[331980]: error: kex_exchange_identification: banner line contains invalid characters
Feb 28 13:58:35 hostname sshd[331981]: error: kex_exchange_identification: banner line contains invalid characters
Feb 28 14:02:44 hostname sshd[332020]: error: kex_exchange_identification: Connection closed by remote host
Feb 28 14:02:45 hostname sshd[332021]: error: kex_exchange_identification: Connection closed by remote host
Feb 28 14:08:50 hostname sshd[332053]: Invalid user admin from openvasscanner port 64282
Feb 28 14:08:50 hostname sshd[332054]: Invalid user peqbmmdx from openvasscanner port 64283
Feb 28 14:08:50 hostname sshd[332056]: Invalid user oracle from openvasscanner port 64284
Feb 28 14:08:50 hostname sshd[332059]: Invalid user karaf from openvasscanner port 64285
Feb 28 14:08:50 hostname sshd[332053]: Received disconnect from openvasscanner port 64282:11: Bye Bye [preauth]
Feb 28 14:08:50 hostname sshd[332053]: Disconnected from invalid user admin openvasscanner port 64282 [preauth]
Feb 28 14:08:50 hostname sshd[332054]: Received disconnect from openvasscanner port 64283:11: Bye Bye [preauth]
Feb 28 14:08:50 hostname sshd[332054]: Disconnected from invalid user peqbmmdx openvasscanner port 64283 [preauth]
Feb 28 14:08:50 hostname sshd[332056]: Received disconnect from openvasscanner port 64284:11: Bye Bye [preauth]
As mentioned previously this is unrelated to any authentication attempt via the provided credentials and done by the scanner by default to “probe” / “fingerprint” (via https://github.com/greenbone/openvas-scanner/blob/v23.16.0/nasl/nasl_builtin_find_service.c) to determine which service is behind which port.
This topic was automatically closed after 86 days. New replies are no longer allowed.