Hello Guys, I want to ship the scanned reports of openvas to a SIEM system. The SIEM system would be wazuh now. So, as soon as there is a new scan by the openvas, I want that data of the report of the scan to be ingested in the SIEM. Could you please suggest me how do I do that? Thanks a lot in advance. Any suggestions would be really helpful. I am using version 22.4 and I built it from the source in Ubuntu 22.04 LTS.
Hello,
I am no expert here, but one quick-and-dirty solution may be:
- Extract the data (reports, vulnerabilities, etc.) using the GVM protocols.
- Ingest the data with Wazuh SIEM or push it into its API (I don’t really know if there is one).
Kind regards,
Hello @victor.sanchez . Thank you so much for your response. I actually tried a different method to push the data to Wazuh. But I used the GVM protocol to extract the report. But there is a problem. I used a report id of the a previous scan made from the GUI to extract the report using GVM. But the xml report I get from the gvm is different from the xml report that I download from the GUI. The report from the GVM does not have any information on the vulnerabilities found and does not contain even the cve info. Could you please tell me why this is the case? And how can I get the exact same report as I see in the GUI? Thank you so much in advance again,
@victor.sanchez Also could you please tell me a how to fetch the report from https:///gmp endpoint to fetch the report. PLease suggest me how to craft the request and authenticate. Sample script would also be very helpful. Thanks a lot
Dear @das,
I used a report id of the a previous scan made from the GUI to extract the report using GVM. But the xml report I get from the gvm is different from the xml report that I download from the GUI.
And how can I get the exact same report as I see in the GUI?
You can retrieve a report given its ID. For instance, if you are using python-gvm, you can go with get_report() method.
The report from the GVM does not have any information on the vulnerabilities found and does not contain even the cve info. Could you please tell me why this is the case?
The report is associated with a scan configuration, a target/s and a task, so you probably want to look further into get_scan(), get_results() or something like that.
Kind regards.
PLease suggest me how to craft the request and authenticate. Sample script would also be very helpful.
You can tune/extend the basic example they provided us with: example.
Replace the last lines (get_tasks(), etc.) with the desired ones.
Regards.
@victor.sanchez Thank you so much for the response. I have already tried this and this is working fine. What if I want to access the api endpoint (http://ip address:9392/gmp) from a remote server to fetch the report. Is that possible?
Sure it is.
You need to set up your machine a little bit. However, I am not going through the details because it may take some time, but I am sure you will sort it out.
Regards.
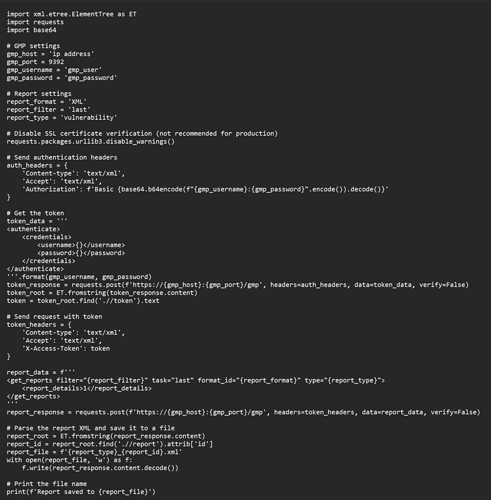
@victor.sanchez I actually tried the following piece of code and getting a ssl wrong version number. Could you please tell me if this is the correct way: