I have a server, with many postgres and oracle services, each service have your own port.
Below, part of the command result: nmap -p 1-65535 -T4 -A -v -sV --allports x.x.x.x
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-08 17:15 -03
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 17:15
Completed NSE at 17:15, 0.00s elapsed
Initiating NSE at 17:15
Completed NSE at 17:15, 0.00s elapsed
Initiating NSE at 17:15
Completed NSE at 17:15, 0.00s elapsed
Initiating Ping Scan at 17:15
Scanning x.x.x.x (x.x.x.x) [2 ports]
Completed Ping Scan at 17:15, 1.64s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 17:15
Completed Parallel DNS resolution of 1 host. at 17:15, 0.06s elapsed
Initiating Connect Scan at 17:15
Scanning x.x.x.x (x.x.x.x) [65535 ports]
Discovered open port 80/tcp on x.x.x.x
Discovered open port 443/tcp on x.x.x.x
Discovered open port 22/tcp on x.x.x.x
Discovered open port 32769/tcp on x.x.x.x
Discovered open port 32782/tcp on x.x.x.x
Discovered open port 32792/tcp on x.x.x.x
Discovered open port 32777/tcp on x.x.x.x
Discovered open port 32785/tcp on x.x.x.x
Discovered open port 32778/tcp on x.x.x.x
Discovered open port 32788/tcp on x.x.x.x
Discovered open port 32770/tcp on x.x.x.x
Discovered open port 38000/tcp on x.x.x.x
Discovered open port 32771/tcp on x.x.x.x
Discovered open port 32774/tcp on x.x.x.x
Discovered open port 32791/tcp on x.x.x.x
Discovered open port 17005/tcp on x.x.x.x
Discovered open port 32768/tcp on x.x.x.x
Discovered open port 32776/tcp on x.x.x.x
Discovered open port 32789/tcp on x.x.x.x
Discovered open port 48702/tcp on x.x.x.x
Discovered open port 32772/tcp on x.x.x.x
Discovered open port 32775/tcp on x.x.x.x
Discovered open port 32783/tcp on x.x.x.x
Discovered open port 32869/tcp on x.x.x.x
Discovered open port 35500/tcp on x.x.x.x
Discovered open port 5555/tcp on x.x.x.x
Completed Connect Scan at 17:15, 12.07s elapsed (65535 total ports)
Initiating Service scan at 17:15
Overriding exclude ports option! Some undesirable ports may be version scanned!
Scanning 26 services on x.x.x.x (x.x.x.x)
Completed Service scan at 17:15, 28.82s elapsed (26 services on 1 host)
NSE: Script scanning x.x.x.x.
Initiating NSE at 17:15
Completed NSE at 17:15, 0.92s elapsed
Initiating NSE at 17:15
Completed NSE at 17:15, 1.70s elapsed
Initiating NSE at 17:15
Completed NSE at 17:15, 0.00s elapsed
....
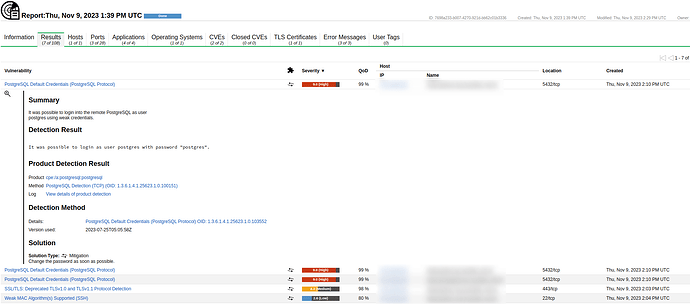
5555/tcp open postgresql PostgreSQL DB 13.2 - 13.4
17005/tcp open postgresql PostgreSQL DB 13.2 - 13.4
32768/tcp open postgresql PostgreSQL DB 13.2 - 13.4
32769/tcp open oracle-tns Oracle TNS listener 18.0.0.0.0 (unauthorized)
32770/tcp open oracle-tns Oracle TNS listener 11.2.0.2.0 (unauthorized)
32771/tcp open oracle-tns Oracle TNS listener 11.2.0.2.0 (unauthorized)
32772/tcp open postgresql PostgreSQL DB 13.2 - 13.4
32774/tcp open postgresql PostgreSQL DB 9.4.13 - 9.4.15 or 9.4.22 - 9.4.26
32775/tcp open postgresql PostgreSQL DB 13.2 - 13.4
32776/tcp open postgresql PostgreSQL DB 10.0 - 10.1 or 10.8 - 10.14
32777/tcp open oracle-tns Oracle TNS listener 11.2.0.2.0 (unauthorized)
32778/tcp open postgresql PostgreSQL DB 9.4.13 - 9.4.15 or 9.4.22 - 9.4.26
32782/tcp open oracle-tns Oracle TNS listener 18.0.0.0.0 (unauthorized)
32783/tcp open oracle-tns Oracle TNS listener 18.0.0.0.0 (unauthorized)
32785/tcp open oracle-tns Oracle TNS listener 18.0.0.0.0 (unauthorized)
32788/tcp open postgresql PostgreSQL DB 13.2 - 13.4
32789/tcp open oracle-tns Oracle TNS listener 18.0.0.0.0 (unauthorized)
32791/tcp open oracle-tns Oracle TNS listener 18.0.0.0.0 (unauthorized)
32792/tcp open oracle-tns Oracle TNS listener 18.0.0.0.0 (unauthorized)
32869/tcp open oracle-tns Oracle TNS listener 18.0.0.0.0 (unauthorized)
35500/tcp open postgresql PostgreSQL DB 13.2 - 13.4
38000/tcp open postgresql PostgreSQL DB 11.3 - 11.9
48702/tcp open postgresql PostgreSQL DB 13.2 - 13.4
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
Initiating NSE at 17:15
Completed NSE at 17:15, 0.00s elapsed
Initiating NSE at 17:15
Completed NSE at 17:15, 0.00s elapsed
Initiating NSE at 17:15
Completed NSE at 17:15, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 45.49 seconds
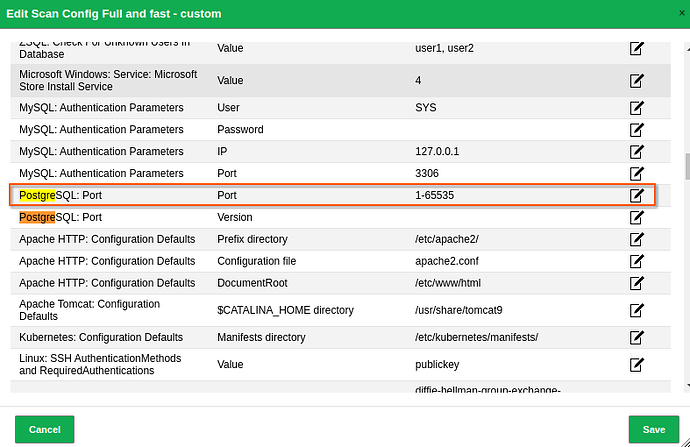
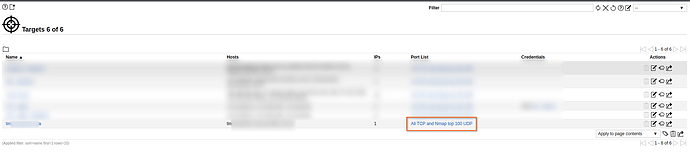
However, GVM does not check these ports, only 5432.
I have already changed the PostgreSQL port in scan configs.