Hello,
I’m currently using GSA version 22.4.0 and gvm package 22.4.1.
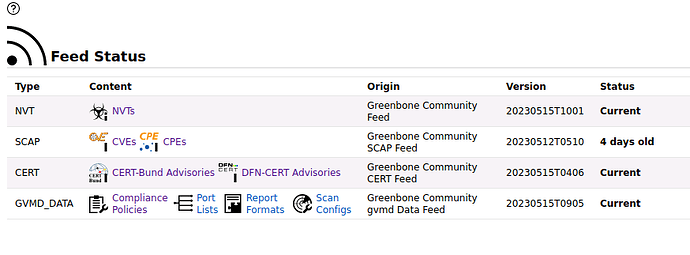
Feed status is OK
I have set up a task with multiple targets, and it seems to be running smoothly. However, I’ve noticed that one of the servers is returning N/A results, while the rest of the servers provide normal findings.
Interestingly, when I ran the same task a few days ago, all servers had normal findings.
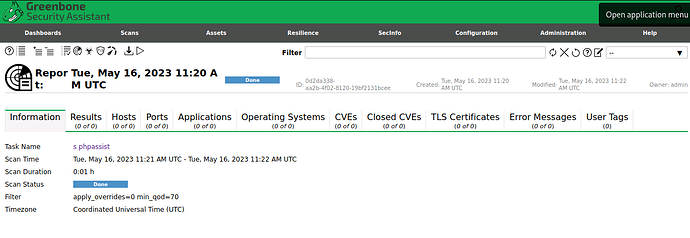
To troubleshoot this issue, I created a separate task specifically for the problematic server. The status of the task is marked as Done, and the severity is listed as N/A. I have included the XML report and relevant logs for reference.
The server is up and running, and can be reached via nmap
$ nmap -Pn -sV x.x.x.x
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-16 14:53 CEST
Nmap scan report for phpassist (x.x.x.x)
Host is up (0.00041s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Win32) OpenSSL/1.0.1h PHP/5.4.31)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.10 ((Win32) OpenSSL/1.0.1h PHP/5.4.31)
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
3306/tcp open mysql MySQL (unauthorized)
3389/tcp open ssl/ms-wbt-server?
5666/tcp open nrpe?
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
I’m having difficulty understanding what could be causing this issue. If anyone has any insights or hints, I would greatly appreciate it.
Thanks for your attention,
<report extension="xml" id="0d2da338-aa2b-4f02-8120-19bf2131bcee" format_id="a994b278-1f62-11e1-96ac-406186ea4fc5" content_type="text/xml"><owner><name>admin</name></owner><name>2023-05-16T11:20:58Z</name><comment></comment><creation_time>2023-05-16T11:20:58Z</creation_time><modification_time>2023-05-16T11:22:57Z</modification_time><writable>0</writable><in_use>0</in_use><task id="9c663b71-c51f-49f4-8452-195168e2c641"><name>s phpassist</name></task><report_format id="a994b278-1f62-11e1-96ac-406186ea4fc5"><name>XML</name></report_format><report id="0d2da338-aa2b-4f02-8120-19bf2131bcee"><gmp><version>22.4</version></gmp><sort><field>severity<order>descending</order></field></sort><filters id="0"><term>apply_overrides=0 min_qod=70 first=1 sort-reverse=severity rows=10000 notes=1 overrides=1</term><filter>High</filter><filter>Medium</filter><filter>Low</filter><filter>Log</filter><keywords><keyword><column>apply_overrides</column><relation>=</relation><value>0</value></keyword><keyword><column>min_qod</column><relation>=</relation><value>70</value></keyword><keyword><column>first</column><relation>=</relation><value>1</value></keyword><keyword><column>sort-reverse</column><relation>=</relation><value>severity</value></keyword><keyword><column>rows</column><relation>=</relation><value>10000</value></keyword><keyword><column>notes</column><relation>=</relation><value>1</value></keyword><keyword><column>overrides</column><relation>=</relation><value>1</value></keyword></keywords></filters><scan_run_status>Done</scan_run_status><hosts><count>0</count></hosts><closed_cves><count>0</count></closed_cves><vulns><count>0</count></vulns><os><count>0</count></os><apps><count>0</count></apps><ssl_certs><count>0</count></ssl_certs><task id="9c663b71-c51f-49f4-8452-195168e2c641"><name>s phpassist</name><comment></comment><target id="0a7efc37-d75d-464e-86b9-c08858a7cbb7"><trash>0</trash><name>t phpassist</name><comment></comment></target><progress>100</progress></task><timestamp>2023-05-16T11:20:58Z</timestamp><scan_start>2023-05-16T11:21:56Z</scan_start><timezone>Coordinated Universal Time</timezone><timezone_abbrev>UTC</timezone_abbrev><ports max="10000" start="1"><count>0</count></ports><results max="10000" start="1"></results><result_count>0<full>0</full><filtered>0</filtered><hole><full>0</full><filtered>0</filtered></hole><info><full>0</full><filtered>0</filtered></info><log><full>0</full><filtered>0</filtered></log><warning><full>0</full><filtered>0</filtered></warning><false_positive><full>0</full><filtered>0</filtered></false_positive></result_count><severity><full>-99.0</full><filtered>-99.0</filtered></severity><scan_end>2023-05-16T11:22:57Z</scan_end><errors><count>0</count></errors><report_format></report_format></report></report>
sudo tail /var/log/gvm/*.log
==> /var/log/gvm/gsad.log <==
==> /var/log/gvm/gvmd.log <==
event task:MESSAGE:2023-05-16 11h17.58 UTC:2331291: Status of task Immediate scan of IP x.x.x.x (85b74db7-1625-4e0a-888c-224377a0eb7d) has changed to Done
event port_list:MESSAGE:2023-05-16 11h20.33 UTC:2334826: Port List p phpassist (bb02b120-4b4e-4c01-8613-113f01b53fb3) has been created by admin
event target:MESSAGE:2023-05-16 11h20.47 UTC:2334976: Target t phpassist (0a7efc37-d75d-464e-86b9-c08858a7cbb7) has been created by admin
event task:MESSAGE:2023-05-16 11h20.52 UTC:2335043: Status of task (9c663b71-c51f-49f4-8452-195168e2c641) has changed to New
event task:MESSAGE:2023-05-16 11h20.52 UTC:2335043: Task s phpassist (9c663b71-c51f-49f4-8452-195168e2c641) has been created by admin
event task:MESSAGE:2023-05-16 11h20.58 UTC:2335112: Status of task s phpassist (9c663b71-c51f-49f4-8452-195168e2c641) has changed to Requested
event task:MESSAGE:2023-05-16 11h20.58 UTC:2335112: Task s phpassist (9c663b71-c51f-49f4-8452-195168e2c641) has been requested to start by admin
event task:MESSAGE:2023-05-16 11h21.50 UTC:2335115: Status of task s phpassist (9c663b71-c51f-49f4-8452-195168e2c641) has changed to Queued
event task:MESSAGE:2023-05-16 11h22.00 UTC:2335115: Status of task s phpassist (9c663b71-c51f-49f4-8452-195168e2c641) has changed to Running
event task:MESSAGE:2023-05-16 11h22.57 UTC:2335115: Status of task s phpassist (9c663b71-c51f-49f4-8452-195168e2c641) has changed to Done
==> /var/log/gvm/openvas.log <==
sd main:MESSAGE:2023-05-16 11h17.13 utc:2332725: Vulnerability scan ef47ab12-8b3d-4310-8540-c0e290c0eedf started: Target has 1 hosts: x.x.x.x, with max_hosts = 20 and max_checks = 4
libgvm boreas:MESSAGE:2023-05-16 11h17.13 utc:2332725: Alive scan ef47ab12-8b3d-4310-8540-c0e290c0eedf started: Target has 1 hosts
libgvm boreas:MESSAGE:2023-05-16 11h17.18 utc:2332725: Alive scan ef47ab12-8b3d-4310-8540-c0e290c0eedf finished in 5 seconds: 0 alive hosts of 1.
sd main:MESSAGE:2023-05-16 11h17.19 utc:2332725: Vulnerability scan ef47ab12-8b3d-4310-8540-c0e290c0eedf finished in 13 seconds: 0 alive hosts of 1
sd main:MESSAGE:2023-05-16 11h22.36 utc:2336298: openvas 22.4.1 started
sd main:MESSAGE:2023-05-16 11h22.36 utc:2336298: attack_network_init: INIT MQTT: SUCCESS
sd main:MESSAGE:2023-05-16 11h22.44 utc:2336298: Vulnerability scan 0d2da338-aa2b-4f02-8120-19bf2131bcee started: Target has 1 hosts: x.x.x.x, with max_hosts = 20 and max_checks = 4
libgvm boreas:MESSAGE:2023-05-16 11h22.44 utc:2336298: Alive scan 0d2da338-aa2b-4f02-8120-19bf2131bcee started: Target has 1 hosts
libgvm boreas:MESSAGE:2023-05-16 11h22.49 utc:2336298: Alive scan 0d2da338-aa2b-4f02-8120-19bf2131bcee finished in 5 seconds: 0 alive hosts of 1.
sd main:MESSAGE:2023-05-16 11h22.50 utc:2336298: Vulnerability scan 0d2da338-aa2b-4f02-8120-19bf2131bcee finished in 14 seconds: 0 alive hosts of 1
==> /var/log/gvm/ospd-openvas.log <==
OSPD[2971] 2023-05-16 11:16:18,452: INFO: (ospd.command.command) Scan ef47ab12-8b3d-4310-8540-c0e290c0eedf added to the queue in position 2.
OSPD[2971] 2023-05-16 11:16:23,082: INFO: (ospd.ospd) Currently 1 queued scans.
OSPD[2971] 2023-05-16 11:16:26,026: INFO: (ospd.ospd) Starting scan ef47ab12-8b3d-4310-8540-c0e290c0eedf.
OSPD[2971] 2023-05-16 11:17:20,076: INFO: (ospd.ospd) ef47ab12-8b3d-4310-8540-c0e290c0eedf: Host scan finished.
OSPD[2971] 2023-05-16 11:17:20,078: INFO: (ospd.ospd) ef47ab12-8b3d-4310-8540-c0e290c0eedf: Scan finished.
OSPD[2971] 2023-05-16 11:21:50,570: INFO: (ospd.command.command) Scan 0d2da338-aa2b-4f02-8120-19bf2131bcee added to the queue in position 2.
OSPD[2971] 2023-05-16 11:21:56,065: INFO: (ospd.ospd) Currently 1 queued scans.
OSPD[2971] 2023-05-16 11:21:56,689: INFO: (ospd.ospd) Starting scan 0d2da338-aa2b-4f02-8120-19bf2131bcee.
OSPD[2971] 2023-05-16 11:22:51,655: INFO: (ospd.ospd) 0d2da338-aa2b-4f02-8120-19bf2131bcee: Host scan finished.
OSPD[2971] 2023-05-16 11:22:51,658: INFO: (ospd.ospd) 0d2da338-aa2b-4f02-8120-19bf2131bcee: Scan finished.