In the greenbone security assistant website, i am able to download the report as a clear text file. how do i use python-gvm to download a report using report_id as a clear text file?
Here is the manual for the command in the docs: https://python-gvm.readthedocs.io/en/latest/api/gmpv208.html#gvm.protocols.gmpv208.Gmp.get_report
get_report(report_id, ***, filter_string=None, filter_id=None, delta_report_id=None, report_format_id=None, ignore_pagination=None, details=True )
Request a single report
PARAMETERS
- report_id (str) – UUID of an existing report
- filter_string (Optional [ str ]) – Filter term to use to filter results in the report
- filter_id (Optional [ str ]) – UUID of filter to use to filter results in the report
- delta_report_id (Optional [ str ]) – UUID of an existing report to compare report to.
- report_format_id (Optional [ Union [ str , ReportFormatType ] ]) – UUID of report format to use or ReportFormatType (enum)
- ignore_pagination (Optional [ bool ]) – Whether to ignore the filter terms “first” and “rows”.
- details (Optional [ bool ]) – Request additional report information details defaults to True
RETURNS
The response. See
send_command()for details.RETURN TYPE Any
hi, i don’t understand, when i use the report_format_id for txt, the content i get is not the same as the content from when i download the text file from the greenbone security assistant
What do you get in the response? How is it different?
I can’t really address a problem without information.
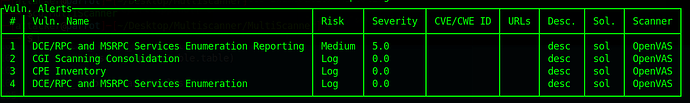
firstly, for debugging, i used this code to print out the vulnerabilites found during a scan and after a scan.
report_response = gmp.get_report(reportID, details=True)
report_response_str = ElementTree.tostring(report_response, encoding=‘unicode’)
report_response_dict = xmltodict.parse(report_response_str)
report_results = report_response_dict.get('get_reports_response', {}).get('report', {}).get('report', {}).get('results', {}).get('result', [])
for vuln in report_results:
name = vuln.get('name')
print('name: ', name)
if scan_results.get(name):
print('--- Duplicate name: ', name)
continue
nvt = vuln.get('nvt', {})
scan_result = {}
scan_result['name'] = name
scan_result['severity'] = float(nvt.get('cvss_base', 0))
scan_result['risk'] = vuln.get('threat')
scan_result['cve_id'] = nvt.get('cve', 'N/A') if nvt.get('cve') != 'NOCVE' else 'N/A'
scan_result['description'] = vuln.get('description')
scan_result['solution'] = nvt.get('solution')
scan_result['reported_by'] = 'OpenVAS'
scan_results[name] = scan_result
def print_report(scan_results):
if not scan_results:
return False
results = list(scan_results.values())
scan_report = []
scan_report.append([ '#', 'Vuln. Name', 'Risk', 'Severity', 'CVE/CWE ID', 'URLs', 'Desc.', 'Sol.', 'Scanner' ])
count = 0
for vuln in sorted(results, key = lambda x: x['severity'], reverse=True):
count += 1
name = vuln['name']
risk = vuln['risk']
severity = vuln['severity']
cve_id = vuln.get('cweid') or vuln.get('cveid', '')
urls = list(vuln.get('urls', []))
description = vuln['description']
solution = vuln['solution']
reported_by = vuln['reported_by']
urls = f'({len(urls)} URLs) {urls[0]}' if urls else ''
scan_report.append([ count, name, risk, severity, cve_id, urls, 'desc', 'sol', reported_by ])
scan_report_table = SingleTable(scan_report)
scan_report_table.title = 'Vuln. Alerts'
print(scan_report_table.table)
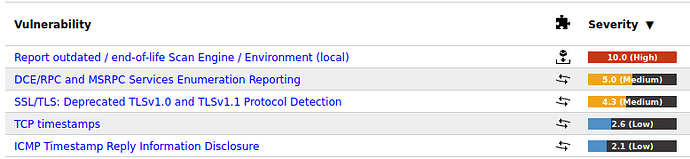
however, after the scan was completed, the vulnerabilites printed out were not all the vulnerabilities the scan found.
these are the results from the greenbone security assistant
Have you tried to apply the filter “levels=hml”?
It’s certainly worth checking whether the filter is causing the XML to be different compared the the GSA report results page, or whether the XML is being parsed correctly by the xmltodict library.
got it, it was the filter. thanks!