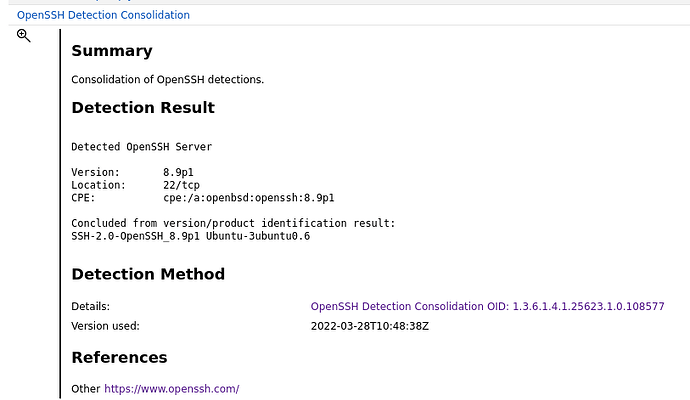
Hi, I have a question regarding the OpenSSH Detection Consolidation.
As I can see the scanner is able to detect the whole version number of OpenSSH, therefore should be able to determine it as not vulnerable to CVE-2023-38408 and CVE-2023-28531, since they are fixed in backport patch. So my question is, why doesn’t GVM/OpenVAS use this information, why do it only use the 8.9p1 part. Is it because it does not consider the whole version number detected remotely as reliable? Does it depend on an authenticated scan to be able to determine it as a false positive?
Further, if the vulnerability is detected as a false positive in a authenticated scan, the 97% QoD vulnerability is not showing, why does the 30% QoD vulnerabilities for the same CVE still show in the results?
Best Regards
Bob