Name: SSL/TLS: Report Vulnerable Cipher Suites for HTTPS
OID: 1.3.6.1.4.1.25623.1.0.108031
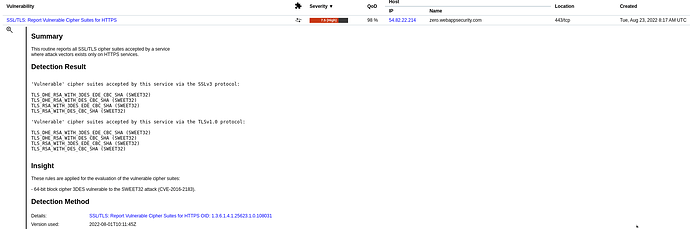
For some reason, the above mentioned VT is not reporting any vulnerabilities anymore, when 3DES/DES ciphers is used.
An example is that the SSL/TLS: Report Supported Cipher Suites reports the following ciphers on SSLv3:
TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA
TLS_DHE_RSA_WITH_AES_128_CBC_SHA
TLS_DHE_RSA_WITH_DES_CBC_SHA
TLS_RSA_WITH_3DES_EDE_CBC_SHA
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_256_CBC_SHA
TLS_RSA_WITH_DES_CBC_SHA
I would have expected the SSL/TLS: Report Vulnerable Cipher Suites for HTTPS VT to be triggered as vulnerable, because of the highlighted ciphers (and quite a few others).
The example is the output from a scan of https://zero.webappsecurity.com/ which is very vulnerable.
Am I misunderstanding something or should’nt the mentioned VT have triggered?
I have tested using GSE v 22.4.0 - NVT feed 20220822T1012.