I’ve installed OpenVAS 22.4 (from source, following the official page) on an Ubuntu 22.04 VM running on a cloud provider. I’ve also added self signed ssl certs and can access the web UI via https, trigger scans etc and all is working.
I’m having a bit of trouble triggering a scan remotely from gvm-cli and would very much appreciate any advice that anyone might have that I can do to make it work. I have provided detailed info about my config and can provide more if needed.
gvm-cli
I want to connect to my OpenVAS VM using the gvm-cli via TLS and my gvm-tools.conf file on the client running gvm-cli contains the following:
[main]
timeout=60
tls_path=/gvm/tls
[gmp]
username=myUsername
password=myPassword
[tls]
certfile=%(tls_path)s/cert.pem
keyfile=%(tls_path)s/cert-key.pem
cafile=%(tls_path)s/ca.pem
port=9390
The command that I’m trying to execute is:
gvm-cli -c /gvm/gvm-tools.conf tls --hostname <REMOTE_OPENVAS_HOST_IP> --xml <get_version/>)
When I execute the above command I get the following error:
gvmtools.cli:[Errno 111] Connection refused
I’ve been reading through this forum and have change the settings in my gsad.service and gvmd.service files as follows:
gsad.service
[Unit]
Description=Greenbone Security Assistant daemon (gsad)
Documentation=man:gsad(8) https://www.greenbone.net
After=network.target gvmd.service
Wants=gvmd.service
[Service]
Type=exec
RuntimeDirectory=gsad
RuntimeDirectoryMode=2775
PIDFile=/run/gsad/gsad.pid
Restart=always
TimeoutStopSec=10
ExecStart=/usr/local/sbin/gsad --foreground --listen=0.0.0.0 --drop-privileges=gvm --port=443 --mlisten=0.0.0.0 --mport=9390 --rport=80 -k /etc/gvm/cert-key.pem -c /etc/gvm/cert.pem
[Install]
WantedBy=multi-user.target
Alias=greenbone-security-assistant.service
gvmd.service
[Unit]
Description=Greenbone Vulnerability Manager daemon (gvmd)
After=network.target networking.service postgresql.service ospd-openvas.service
Wants=postgresql.service ospd-openvas.service
Documentation=man:gvmd(8)
ConditionKernelCommandLine=!recovery
[Service]
Type=exec
User=gvm
Group=gvm
PIDFile=/run/gvmd/gvmd.pid
RuntimeDirectory=gvmd
RuntimeDirectoryMode=2775
ExecStart=/usr/local/sbin/gvmd --foreground --osp-vt-update=/run/ospd/ospd-openvas.sock --listen-group=gvm
Restart=always
TimeoutStopSec=10
[Install]
WantedBy=multi-user.target
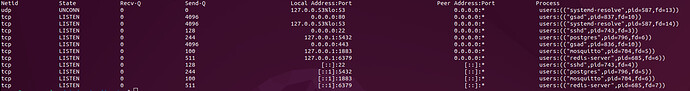
When I run ss -utlpn I can see that gvmd is not running on port 9390
I’ve read through this forum and try various configs in my gvmd.service file, but I haven’t been able to get it working so far.
I would appreciate any comments/advice if anyone knows what might be reason (based on the info) that my gvmd is not running on port 9390?